DevOps Training
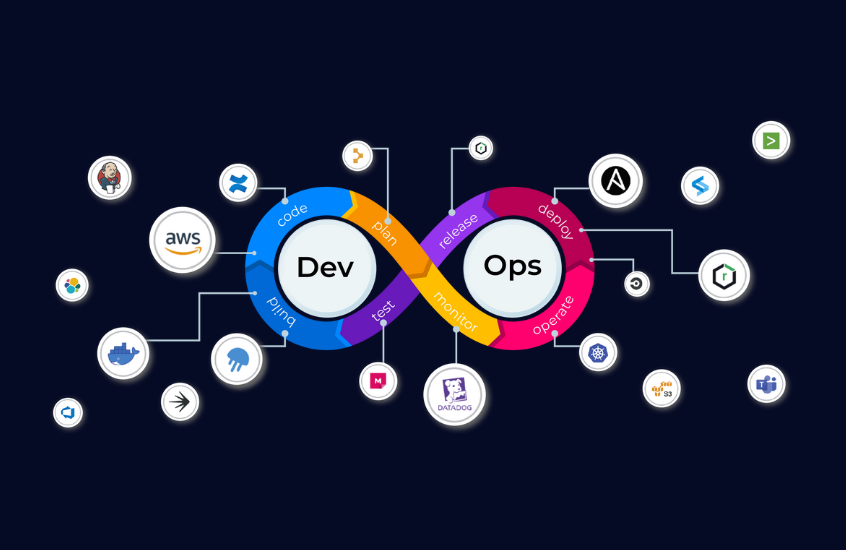
Temika Cyber presents a DevOps Training program designed to help companies and individuals improve the efficiency of software and operational development processes. This service includes comprehensive training about basic concepts up to DevOps applications using technology and modern tools like Docker, Kubernetes, Jenkins, Ansible, and others.
Process of Digital Forensic & Incident Response
Process of DevOps Training:
1. Initial Consultation
We understand your need to determine the proper training focus.
2. Material Development
The curriculum is adjusted to your needs and goals.
3. Training Implementation
Interactive training sessions are done online or onsite with experienced instructor guides.
4. Hands-on Practice
Participant learned through simulation of real projects and case studies.
5. Evaluation
We evaluate the training results and provide feedback for improvement.
6. Certification
The participants who completed the training get official certificates and post-training support.
Why are DevOps Training Penting Important?
Benefit of DevOps Training:
- Contact Us
Ready to
Get Started?
Book a free consultation today, and we’ll write you back within 24 hours.
